Measures to ensure Cyber Security in a serverless environment
There is a lot that can be said and written when it comes to cyber security. But in the past few years, this game has completely changed with the increased remote setup and the uncertainty till which it will continue. Cyber Security in business has taken a different path altogether. How good it will be to learn about the measures that can be taken to ensure Cyber Security in a serverless environment.
Serverless Environment: Brief Introduction
A serverless environment/architecture is a manner in which applications are run without any physical server or without a specific infrastructure. It is a virtual setup where the server along with the applications is managed via cloud computing. It has innumerable benefits.
- It saves the cost of setting up a proper physical server and its maintenance.
- The overall cost is reduced.
- It fastens the process of deployment and updates.
- The serverless environment is wide and expandable to a great extent.
Apart from this, you can have other benefits such as:
- You can work anywhere around the world irrespective of your office’s location.
- It gives you the flexibility of making any place your home (of course abiding by your organization’s rules).
- It saves a lot of time in terms of commuting.
Serverless Environment: Cyber Security Threats
In a serverless environment, vulnerabilities of attack increase to a great extent which is an indication of taking quick and advanced actions to ensure cyber security in a business. Let’s have a look at some of the cyber security threats in a serverless environment.
- Injection Flaws: The most common cause of cyber security threats is function event-data injection. Unlike web environments, in serverless environments, it is difficult to figure out secure and non-trusted paths. In such cases, the interpreter takes untrusted information and executes it. This makes the whole environment quite vulnerable to attacks. The most common examples of injection flaws in a serverless environment are:
- Function run time code injection (happens in node.js/javascript, python, C##, Java, etc.)
- SQL injection
- OS command injections and so on.
- Authentication Gets Broken: In a serverless environment, exist a number of functions as it is a microservices-type environment. Now each of these functions is not completely secure as they can promote exposure of public web APIs. Some of them can act as proxy functions for various processes thus exposing the entry points of the environment and posing a great threat to cyber security.
- Incorrect Configuration Settings: As we all know that the concept of a serverless environment is not very old, hence, it is still a learning curve for computer architects and engineers to set a properly configured environment. This may lead to misconfiguration or incorrect configuration of the environment, which in turn increases the risk of loopholes that can compromise cyber security.
- Granting High-Level Permissions: Giving high-level permissions for accessing confidential data via a serverless environment is another way of inviting threats. This could result in the mishandling of information by performing unintended operations such as “executing system function”.

- Improper Monitoring of Logs: Though most organizations make it a point to constantly monitor the logs/activities of users, especially in a serverless environment, it is quite possible that they lag behind in it. As monitoring of logs is done in real-time, missing out on any suspicious activity can result in a mismatched audit trail, thus increasing the risk of cyber-attacks.
- Untrusted Third-Party Dependencies: With the latest open-source frameworks, app development has become easier, but it has also made the serverless environment vulnerable. It takes just a small code to inject a virus while a developer is calling a third-party service through API calls.
Now that we have discussed some of the possible security threats to a serverless environment, let’s have a look at the measures to strengthen it.
How to Make a Serverless Environment More Reliable?
Several measures have been taken by organizations to ensure maximum cyber security in a business. Some of the most remarkable ones are listed below:
- Permission at Every Step: As mentioned above, granting high-level permission makes the environment more vulnerable to threats. Hence, introducing permissions at every function helps in the micromanagement of cyber security. The more restrictions are imposed on the usage of functions, the less chance of attack there is.
- Checking Every Bit of Data Carefully: No matter how reliable the source of data is, we should keep checks at every point by properly evaluating every program and every line of code. It goes without saying that even the finest developers can miss damages like file intrusion attacks, so evaluation at even the smallest step is compulsory.
- Collection of Real-time Security Events: It is highly recommended by experts to have proper data monitoring of real-time security events. This helps in detecting threats and stopping them at a very initial stage. Taking advantage of AWS services like AWS X-Ray, Amazon CloudTrail, and Amazon CloudWatch is a great option to avail of third-party security services.
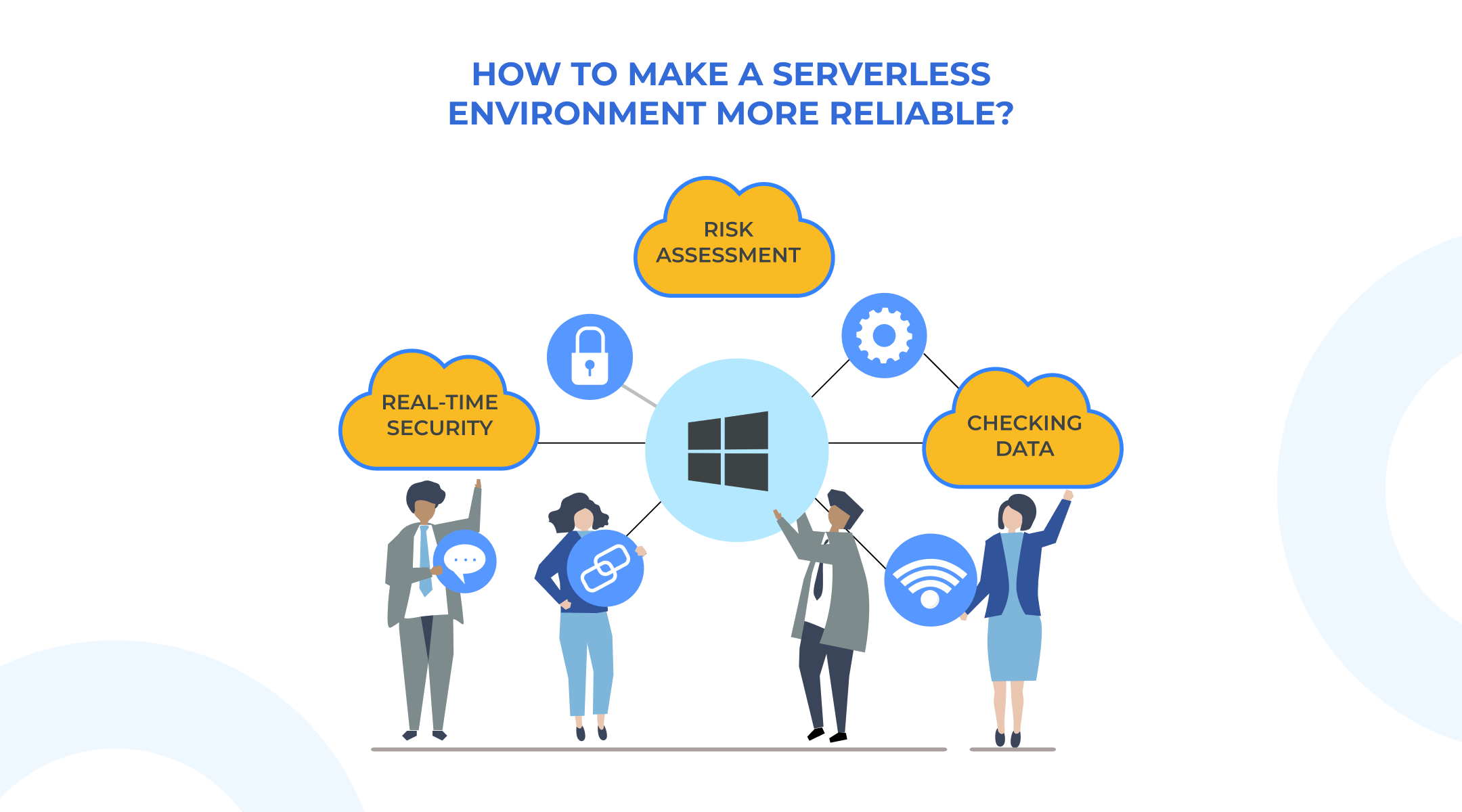
- Frequent Risk Assessment: A serverless environment can expose confidential data through various functions. Therefore, it is important to conduct risk assessment exercises on a regular basis. Further, data encryption tightens the boundaries for any sort of cyber-attack.
- Introduce Secure Authentication: Make full use of enormously beneficial tools like Microsoft’s Azure AD. These tools help in creating a complex security system for a serverless environment. You can also enforce steps that can nullify the effect of a potential threat.
- Privatization of API Gateways: You can set a limit for the number of clients to access your API gateways. The smaller the number of clients the less vulnerable API gateways will become. Hence, make these gateways are private and completely deprived of any sort of cyber-attack.
Apart from these measures, there are general safeguarding techniques, like training of staff, endpoint protection, continuous data backup, usage of secured Wi-Fi connection, etc. that encourage cyber security in a business.
Future of serverless environment
With the businesses reaching the pinnacle of success with serverless environment setup, things have taken a different route altogether. While earlier serverless environment was restricted to a few jobs, now it has become more and more popular for things like batch and transaction processing. So, workloads like scheduling an event and tracking of any failure protocols can be done with utmost ease with serverless environment.
With more organizations adopting to serverless environment, there are various benefits of it.
Cost Saving: A serverless environment comes down to zero when there is no request being processed. This helps in saving the overall cost by reduced use of services.
Boon for DevOps: Setting up a physical environment is much of a tedious task for developers, but with serverless environment the complete operation can be done easily.
Easy use of Service: With serverless environment starting any service is easier with just a single line of code. So, another benefit for the developers.
Similarly, there are other benefits of serverless environment like high scalability, reduced latency, and so on. And with all this in consideration, cyber security has a vast role to play. In case you want to explore more about handling security in a serverless environment, visit www.fibonalabs.com and read our latest blog.



