Penetration Testing: Step-by-Step Guide and Methods
Penetration testing, also known as Pen testing aims to make unauthorized attempts to violate the security and integrity of the system, application, network, or database.
The goal of pen testing is to outsmart attackers or hackers by exposing weak links or security gaps in the system.
Why Penetration Testing is Required?
- It verifies the ability of the system to protect its networks, applications, endpoints, and users against both internal and external threats.
- It aims to secure the system controls and avoid any attempts of unauthorized access.
- Identify the environment that an attacker can use to break the security of the system.
- Identify the application areas which are vulnerable to attacks.
Penetration Testing Phases
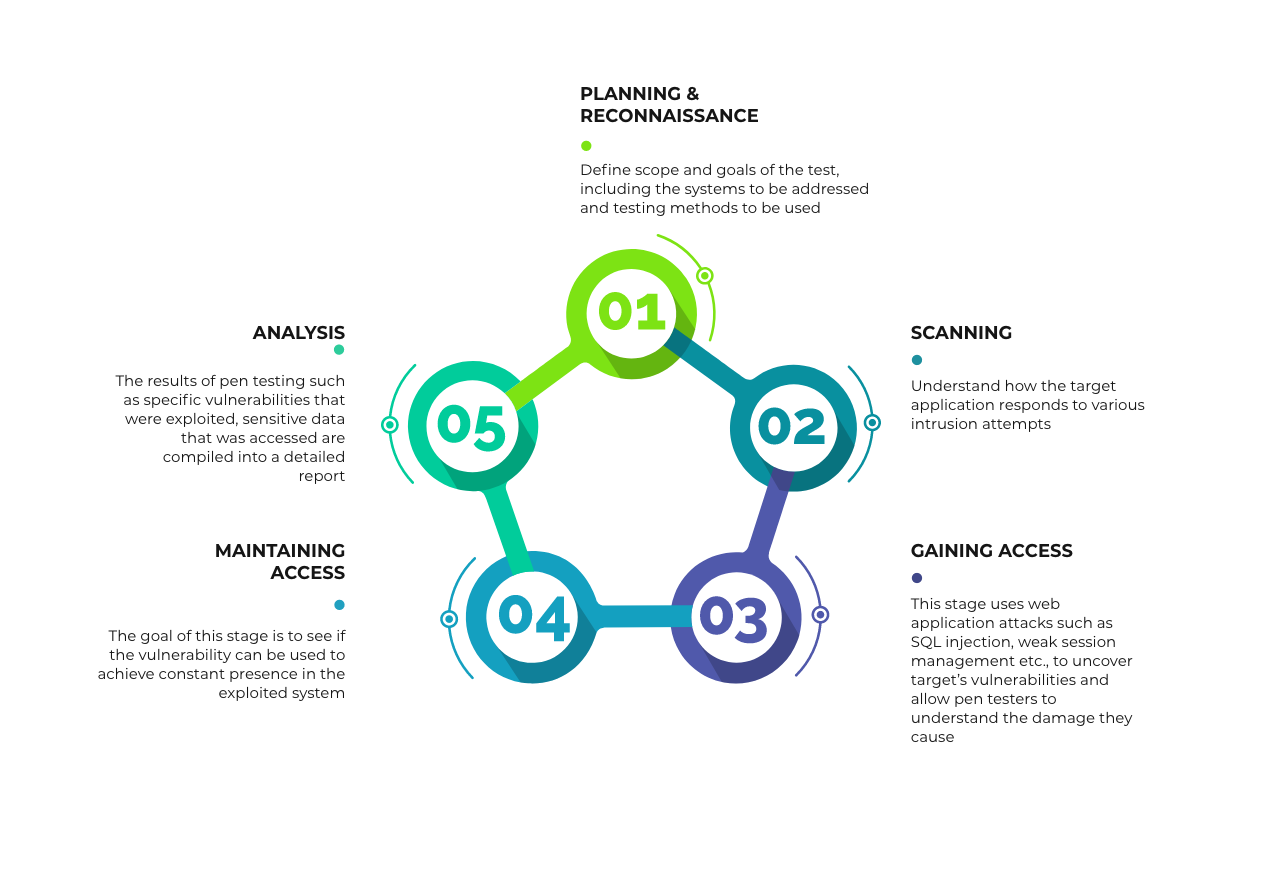
Approaches in Penetration Testing
The level of information provided to the pen tester will determine their approach as well as the scope of the project.

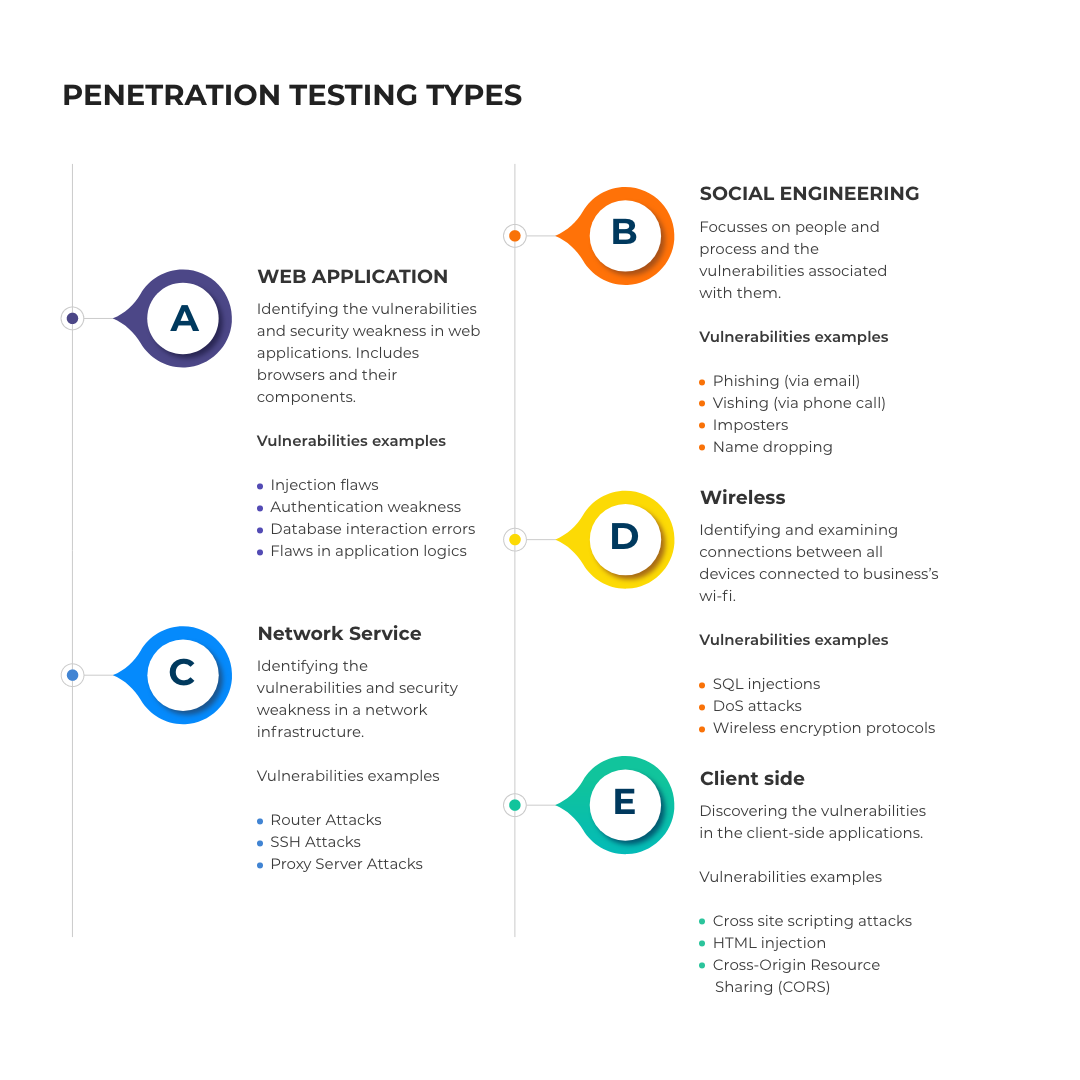
Penetration Testing Types
Primarily, there are 5 main types of penetration testing available, each of them resolving different types of security issues. Therefore, it is important to understand the differences, to know which type of test shall meet their system requirements and objectives.
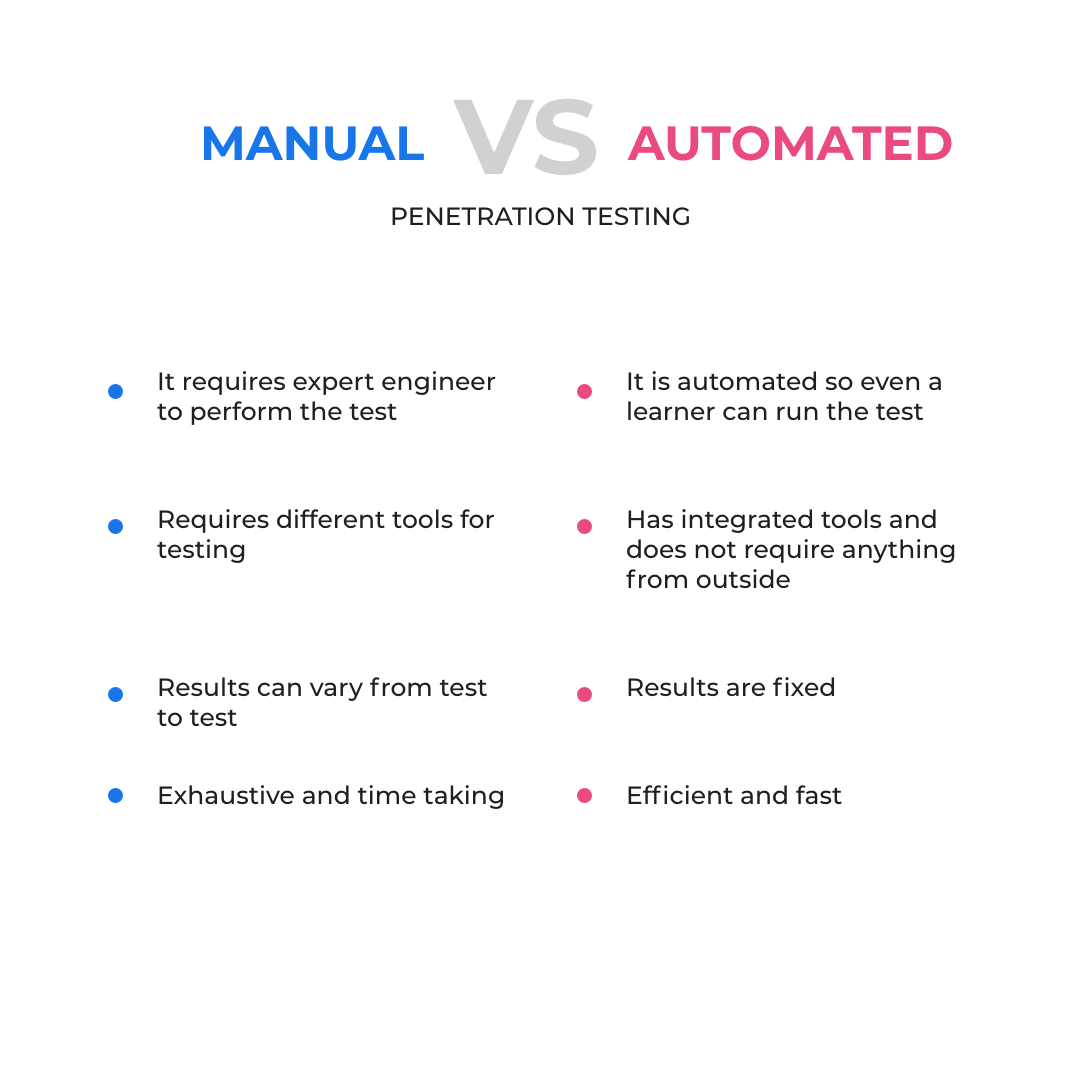
Manual vs Automated Penetration Testing
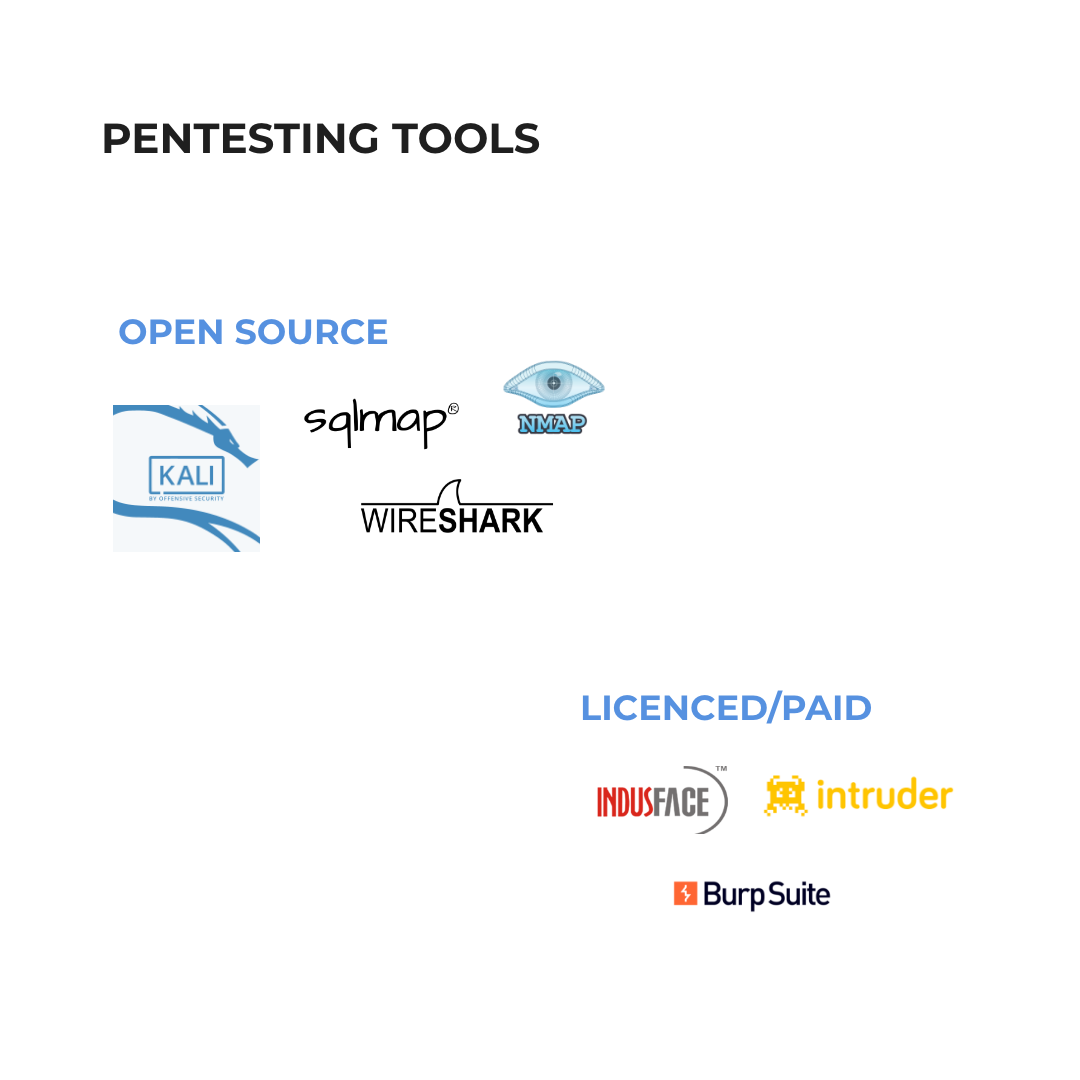
Advantages of Penetration Testing
- Helps to find vulnerabilities and fix them before a hacker makes an attack.
- Help reveal problems that didn’t even know existed.
- Test the application’s cyber-defense capability.
- Ensures business continuity.
- Avoid costly data breaches
Summary
Through pen testing, security professionals can effectively identify any vulnerabilities or weaknesses. It helps them to test the security of not only the servers, workstations, mobile devices, web applications, and network design but also the working practices of IT staff and users. The pen testing tools help you gain fast insight into the areas of highest risk so that you may effectively plan for taking the precautions needed to secure vital data.



